
【iMessage苹果推送】苹果群发Provisioning Profile文件所使用的Certificate是雷同的_profile文件不支持推消息功能_IMEAX的博客CSDN博客
1 Answer Sorted by: 75 Setting net.core.somaxconn to higher values is only needed on highloaded servers where new connection rate is so high/bursty that having 128 (50% more in BSD's: 128 backlog + 64 half-open) not-yet-accepted connections is considered normal. Or when you need to delegate definition of "normal" to an applications itself.

TCP/IP协议中backlog参数 程序员大本营
net.core.somaxconn = 8192. アプリケーションは net.core.somaxconn カーネルパラメーターで指定したよりも多くのリッスンバックログを要求することができますが、カーネルはこのパラメーターで設定した番号にアプリケーションを制限することに注意してください。
The Mysterious Container net.core.somaxconn (2022)
5 Answers Sorted by: 509 Maximum number of connections are impacted by certain limits on both client & server sides, albeit a little differently. On the client side: Increase the ephermal port range, and decrease the tcp_fin_timeout To find out the default values: sysctl net.ipv4.ip_local_port_range sysctl net.ipv4.tcp_fin_timeout

路由包含号导致的nginx_58房产Nginx 网络调优实践CSDN博客
docker run \--sysctl net.core.somaxconn=1024 \--sysctl net.ipv4.tw_reuse=1 \ someimage. Similarly, recent enough versions of Docker support sysctls in compose files for docker-compose and swarm mode:
[OS/Linux] 千千寰宇 博客园
Since the container's somaxconn value is the default of 128, Redis was not able to use a value of 511. In a non-containerized world, changing this kernel parameter would be as simple as placing the following into the /etc/sysctl.conf file. net.core.somaxconn=1024. After adding the above, you would simply execute sysctl -p. However, in the.

TCP 队列 ck_2016 博客园
Scanario: I have a container image that needs to run with net.core.somaxconn > default_value. I am using Kubernetes to deploy and run in GCE. The nodes (vms) in my cluster are configured with correct net.core.somaxconn value. Now the challenge is to start the docker container with flag --sysctl=net.core.somaxconn=4096 from kubernetes. I cannot seem to find the proper documentation to achieve this.

The Problem How To Check Net Core Somaxconn In Linux
net.core.rmem_max: TCPとUDPの受信バッファのデフォルトサイズと最大サイズ: 〇: net.core.somaxconn: backlog値のhard limit: 〇: net.core.netdev_max_backlog: NIC に対する受信パケットの最大キューイング数: 〇: net.ipv4.tcp_max_syn_backlog
How do I add net.core.somaxconn to the whitelist? · Issue 94249 · · GitHub
For suggestions, see Metalink Note:249213.1 and Note:265194.1. On Red Hat Enterprise Linux systems the default range of IP port numbers that are allowed for TCP and UDP traffic on the server is too low for 9i and 10g systems. Oracle recommends the following port range: # sysctl -w net.ipv4.ip_local_port_range="1024 65000".

你竟然呵呵我,超全Linux网络内核参数优化秘籍你有吗? 知乎
Nowadays net.core.somaxconn caps both queue sizes. On our servers we set it to 16k: $ sysctl net.core.somaxconn net.core.somaxconn = 16384 Perfect backlog value. Knowing all that, we might ask the question - what is the ideal backlog parameter value? The answer is: it depends. For the majority of trivial TCP Servers it doesn't really matter.
is set to the lower value of 128 · Issue 256 · dockerlibrary
sysctl -p. Show value for a single parameter parameter-name. sysctl parameter-name. Change value for a single parameter parameter-name without editing sysctl.conf manually. sysctl -w parameter-name=parameter-value. Above command will overwrite any previous modifications to parameter-name. Also, you may need to surround parameter-value with quotes.

Notas de estudio de Redis solución al problema de advertencia de inicio programador clic
net.core.somaxconn = 4096 net.ipv4.tcp_max_syn_backlog = 8192 net.ipv4.ip_local_port_range = 30000 64999 net.ipv4.tcp_tw_reuse = 1 net.ipv4.tcp_tw_recycle = 1 net.ipv4.tcp_timestamps = 1 net.ipv4.tcp_syn_retries = 8 Fore more information, see the following SAP Notes: SAP Note 2382421; SAP Note 2205917; SAP HANA Parameters

linux安装部署环境(jdk,nacos,nginx,mysql,redis)_linux nginx redisCSDN博客
The following example uses the pod securityContext to set a safe sysctl kernel.shm_rmid_forced and two unsafe sysctls, net.core.somaxconn and kernel.msgmax. There is no distinction between safe and unsafe sysctls in the specification. To avoid destabilizing your operating system, modify sysctl parameters only after you understand their effects..
[OS/Linux] 千千寰宇 博客园
Forward Packets between interfaces. This variable is special, its change resets all configuration parameters to their default state (RFC1122 for hosts, RFC1812 for routers) ip_default_ttl - INTEGER Default value of TTL field (Time To Live) for outgoing (but not forwarded) IP packets. Should be between 1 and 255 inclusive.
[OS/Linux] 千千寰宇 博客园
3. On my system it's defined in bits/socket.h. /* Maximum queue length specifiable by listen. */ #define SOMAXCONN 128. According to this, you don't need to use SOMAXCONN. Just specify number you want and it will be limited to actual maximum. Share. Improve this answer. Follow. edited May 23, 2017 at 11:45.
net.core.somaxconnについて調べてみた 祈れ、そして働け ~ Ora et labora
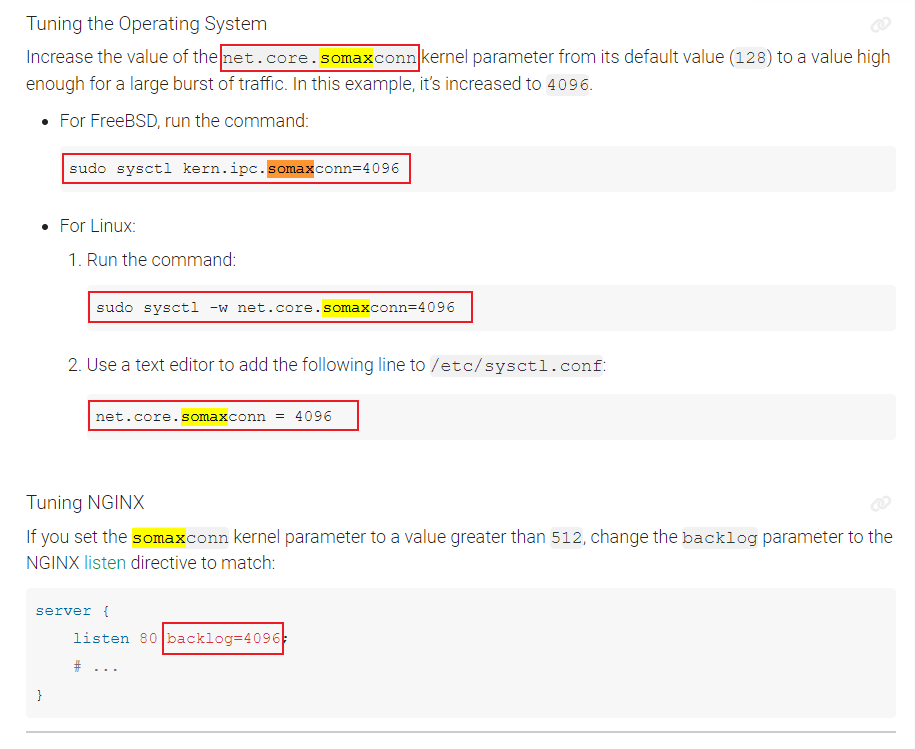
The net.core.somaxconn parameter can be set to any value between 128 and 65535. As we've mentioned, it is generally recommended to set it to a value that is equal to or slightly larger than the backlog value of NGINX.

小麦苗DBA宝典
somaxconn is a kernel parameter in Linux that determines the maximum number of connections that can be queued in the TCP/IP stack backlog per socket. We can assign a 16 bits value which is equivalent to 65535 in RHEL 6 & RHEL 7 but in RHEL 8, we can increase the value to 32 bits. Root Cause